This is Omdia’s latest annual report covering Data Privacy Day, which fell on January 28. Approximately two-thirds of security breaches involve data exposure, many of these of personally identifiable information.
Summary
Catalyst
This is Omdia’s latest annual report covering Data Privacy Day, which fell on January 28. Sadly, there are continued breaches of data privacy, and Omdia notes that approximately two-thirds of security breaches involve data exposure, many of these of personally identifiable information (PII). Data Privacy Day serves to highlight the inadequacies of data protection and to support the confidentiality of information.
Omdia view
The marking of Data Privacy Day is designed to raise awareness of data privacy and promote good practice to protect information.
Many (not all) organizations now recognize that it is not a question of if but when they will suffer a security breach. Data exposure will continue to account for around two-thirds of breach outcomes. Organizations will continue to fail customers’ data privacy expectations, and many of these failures could have been prevented by cyber-hygiene. However, cyber-hygiene is not easy because of the complexity of cybersecurity. Regulators continually push for improvements to improve data privacy outcomes. Some consumers are becoming increasingly savvy about data privacy, but others “happily” give away their personal information in exchange for free services.
Ultimately, organizations must be resilient. They must be resilient in their operations and resilient in data privacy. Today’s world is digitally dependent, which is no bad thing, but digital dependence demands digital resilience. Planning for the inevitable means that organizations are better prepared to deal with security incidents and breaches when it comes to data privacy.
Key messages
- Data exposure will continue to account for the vast majority of breach outcomes.
- Regulators lead demands for improvement, and there are increased consumer expectations.
- The need for resilience must be the foundation of data privacy efforts.
Recommendations
- Review current cyber-hygiene capabilities and prioritize the gaps. Resilience is key. Many enterprises are confident in their security controls, but many enterprises breach data privacy regulations. Control of the information footprint is essential to provide the appropriate protection. Review your security controls around data privacy.
- Determine where responsibilities lie and practice responding to data privacy breaches. Organizations now accept it is not a case of if but when a security incident or breach will happen. Knowing where responsibilities lie when that attack does happen and practicing how the response will take place will leave the organization better prepared for the inevitable.
- Consider how the security workforce can be augmented. Many organizations use external providers—managed security services—to supplement their security workforce. Some of this augmentation supports the day-to-day running of the security function; in some organizations additional services support the response to a security incident or breach.
Data exposure will continue to account for the vast majority of breach outcomes
Organizations will continue to fail customers’ data privacy expectations
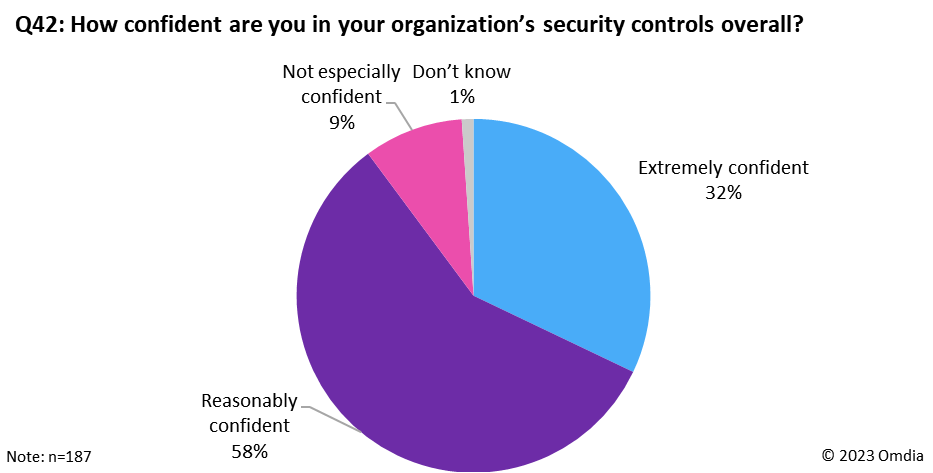
Omdia’s Cybersecurity Decision Maker survey, conducted in 2Q22, found that 32% of organizations are “extremely confident” in their organization’s security controls, and a further 58% describe themselves as “reasonably confident” (see Figure 1).
Figure 1: Omdia Cybersecurity Decision Maker survey, confidence in security controls
 Source: Omdia Cybersecurity Decision Maker survey
Source: Omdia Cybersecurity Decision Maker survey
However, this confidence is likely misplaced. Panaseer’s “2023 Security Leaders Peer Report” notes that control failure remains a major preventable cause of breaches. According to the study, 79% of enterprises have experienced cybersecurity incidents that should have been prevented with current safeguards, and around 90% of security leaders state that failure of an expected control is the primary reason for breaches.
Further evidence of overconfidence in existing security controls can be found in the Cybersecurity Decision Maker survey, which shows that 77% of organizations have suffered numerous security incidents and breaches, some with severe impact on the organization.
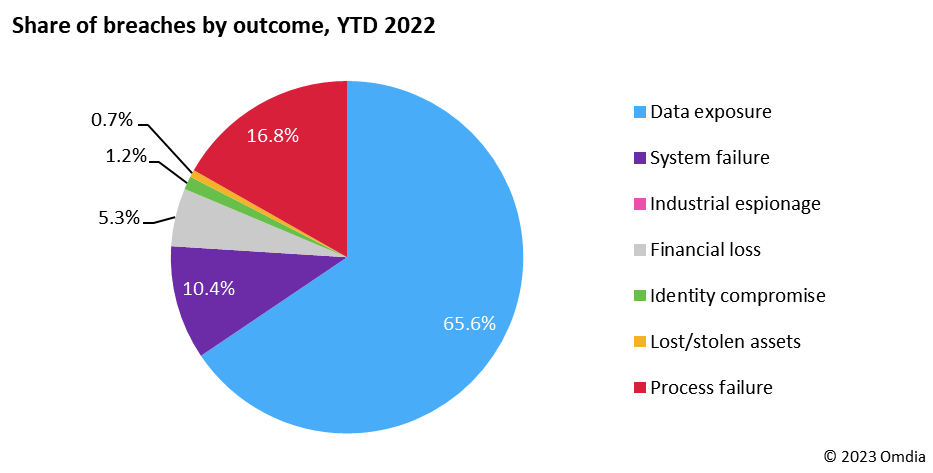
Some of these security breaches will be included in Omdia’s Security Breaches Tracker. This data looks at the leading outcome of security breaches, and in the breaches reported during the first nine months of 2022, for 66% of breaches tracked this was data exposure (see Figure 2).
Figure 2: Omdia Security Breaches Tracker, share of breaches by outcome, 1Q22–3Q22
 Source: Omdia Security Breaches Tracker
Source: Omdia Security Breaches Tracker
Looking back at the historical data to 2019, we see that approximately two-thirds of breaches have consistently resulted in data exposure: 68 % in 2021, 67% in 2020, and 64% in 2019. Thus, it is not a stretch to say that organizations will continue to fail customers’ data privacy expectations.
Many breaches drink from the data privacy cup
Omdia’s Security Breaches Tracker shows that at the time of writing there were around 2.3 billion records affected by breaches reported in the first nine months of 2022.
Table 1: Omdia Security Breaches Tracker, 1Q22–3Q22
|
Primary breach method |
Description |
Number of records exposed |
|
Hacking |
An attempt to exploit a computer system or a private network inside a computer to gain unauthorized access to or control over computer network security systems for illicit purposes |
1.3 billion |
|
Accidental exposure |
Information or systems are exposed inadvertently, leading to a compromise opportunity |
850 million |
|
Ransomware |
A type of malware that infects, locks, or takes control of a system and demands a ransom (usually cryptocurrency) to undo it; ransomware attacks and infects a computer with the intention of extorting money from its owner |
50 million |
|
Insider |
Anyone with access to systems and information that those outside do not; insiders can be malicious, sloppy/negligent, or unintentional |
22.5 million |
|
Supply chain |
Also called a value-chain or third-party attack, occurs when someone infiltrates an organization’s system(s) through an outside partner or provider with access to the organization's systems/data |
5 million |
|
Phishing |
Using email (typically) to trick the recipient into giving away information or access to information, such as credit card numbers, personal identification, and account usernames and passwords |
1.8 million |
Source: Omdia
Although not all these breaches are of records with an impact on data privacy, many are.
One example of a hacking attack resulting in data exposure is that on the Shanghai National Police, reported in early July 2022. The Shanghai National Police suffered a major data breach when a hacker named ChinaDan stole the information of approximately 1 billion Chinese citizens directly from the Shanghai National Police database. This accounts for the majority of the records exposed by the hacking breach method in Table 1.
Table 1 also shows the significant volume of breached records as a result of accidental exposure. By far the largest breach in this group is that of Xinai Electronics, based in China. It left a database that included the personal information of around 800 million people exposed on the internet without any password protection. There will always be malicious actors looking to capitalize on mistakes such as these, and even if the accidental exposure is spotted earlier by friendly actors, it may well still be a breach of data privacy.
Although ransomware appears a little lower down on the list, the Xinai breach distorts the data somewhat. Omdia does expect that ransomware cases will increase as hacker groups continue to innovate their attacks. This is because there are both lucrative financial benefits and a low barrier to entry to ransomware as a service (RaaS), a business model between ransomware operators and affiliates where the affiliates pay a fee to deploy ransomware kits developed by the operators. RaaS carries the threat of an onslaught of cyberthreats toward the end of 2022 and throughout 2023, given its accessibility even to individuals without technical prerequisites.
Ransomware affiliates will need only to execute the ransomware after identifying a target and setting a ransom demand: it is the RaaS operators that are the masterminds behind the ransomware packages with dedicated command and control dashboards, victim payment portals, and management of dedicated leak sites. The affiliates are the ones communicating with the victims and managing the decryption keys.
UpGuard, a software firm focused on helping businesses to mitigate third-party cybersecurity risks, noted the attractive returns for RaaS affiliates. The Netwalker ransomware, notorious for its victims, which include the Austrian city of Weiz; Pakistan’s largest private power utility company, K-Electric; and Argentina’s immigration agency, pays its affiliates up to 80% of each successful ransom payment following the deployment of the ransomware. Netwalker ransomware attacks use legitimate-looking phishing emails to trick recipients into clicking links and downloading attachments as an entry to initiate the attacks. This being the case, phishing attacks may see a rise as ransomware cases increase, highlighting the interplay between the different breach methods employed in attacks executed by the threat actors.
Infamous RaaS groups include DarkSide, REvil/Sodinokibi, and LockBit. In the first half of 2022, LockBit emerged as one of the most deployed ransomwares, with attacks aimed at the Ministry of Justice in France (January 2022), the secretary of state for finance of Rio de Janeiro (April 2022), and Foxconn Baja California, Foxconn’s production base of medical devices, consumer electronics, and industrial operations (May 2022).
There is also the December 2022 ransomware attack on the SickKids hospital for children in Toronto; although the RaaS supplier has issued an apology and offered a free decryptor, the actions of the affiliate (the RaaS customer) mean that a complete data and systems recovery is unlikely for the hospital. Moral lines have been crossed for a long time.
Basic cyber-hygiene might have prevented many data privacy breaches, but “basic” does not mean “easy”
Cyber-hygiene is not a one-and-done task. It requires constant review and updating, because malicious actors are also constantly reviewing and updating their offensive capabilities. ITC Secure, a cybersecurity services organization, comments that the sophistication of cyberattacks continuously increases, with attackers taking more advantage of artificial intelligence and machine learning. ITC also says that increasing focus on identity is essential if organizations are to improve their cyber-hygiene. Omdia noted that “identity is the perimeter” back in 2021, but many organizations are still getting to grips with hybrid working and the need for individuals to be secure irrespective of working location.
To return to the Panaseer report, when asked for what reasons controls might fail, survey respondents identified a lack of internal resources and an inability to evidence control remediation. Both factors require people to execute, and there has been an omnipresent shortage of people to work in cybersecurity.
In its annual Cybersecurity Workforce Study, released in October 2022, (ISC)² made its highest ever estimate of the size of the cybersecurity workforce, putting it at 4.7 million people. However, the same study also estimated a workforce shortage of 3.4 million worldwide. An overall security workforce shortage is also recognized in Omdia’s Cybersecurity Decision Maker survey, with 47% of survey respondents reporting this as one of the biggest issues they are facing (see Figure 3).
Figure 3: Omdia Cybersecurity Decision Maker survey, issues most affecting security functions
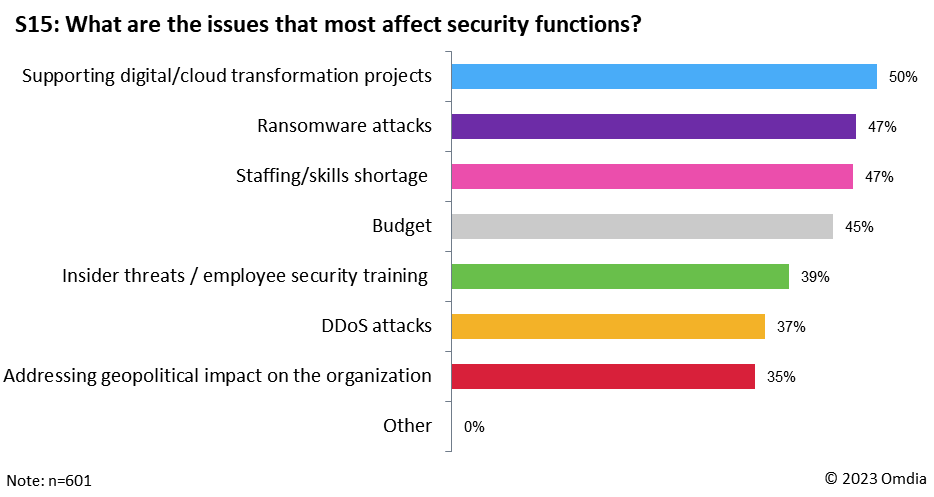 Source: Omdia Cybersecurity Decision Maker survey 2022
Source: Omdia Cybersecurity Decision Maker survey 2022
Cyber-hygiene can be defined as the good practice that all organizations can follow to minimize the opportunity for cybersecurity incidents to materialize. Examples include timely patching, password management, backups, and much more besides. Figure 3 also shows the other challenges faced by the security function, including the rapid pace of digital projects. This affects its ability to provide appropriate security controls in a timely manner, especially when security is not part of the planning and testing process.
In addition to the workforce shortage there are other reasons why cyber-hygiene is not straightforward and why breaches of data privacy happen:
- Data location. An organization’s data can be in locations far and wide. As it progresses through the information lifecycle—create, process, store, transmit, and (hopefully) destroy—it frequently becomes a copy of itself: developers might use it for testing, and so on. If an organization does not know where its data is, it cannot possibly hope to protect it appropriately.
- Responsibility. System patching, for example, might not be the responsibility of the security function in an organization; it might sit in the IT function, which might be separate. Omdia’s Cybersecurity Decision Maker survey noted that 40% of an organization’s most senior security executives report into technical roles (e.g., chief information officer, chief technology officer). The remaining 60% report into nontechnical roles, which requires collaboration and coordination between various reporting lines. Cybersecurity often has blurred lines between one organizational function and another.
- Complexity. Cybersecurity is not just one thing: it is data security, identity, authentication, access, network security, content security, security operations, security management, device security, the list goes on. Even data security has three major categories according to Omdia’s cybersecurity taxonomy: data discovery, data governance, and data protection. Covering the bases requires people and expertise in different parts of cybersecurity; these people can be both difficult to find and expensive thanks to the workforce shortage.
Of course, there are many more reasons why basic cyber-hygiene is difficult to achieve, but the above give some flavor to the challenges being faced. ITC Secure makes the valid point that CISOs and CIOs and their teams are overloaded and must prioritize.
Failures in cyber-hygiene can lead to opportunities for security incidents and breaches, and around two-thirds of these breaches result in data exposure, most of it of customers’ PII. Not only does this erode customer trust in the organization, it also opens the organization to potential regulatory breaches and fines.
Regulators lead demand for improvement, plus increased consumer expectations
Data privacy legislation applicable in many parts of the world
Data privacy legislation has been enacted around the world; some examples are shown in Table 2.
Table 2: Examples of data privacy legislation
|
Legislation |
Location |
Description |
|
General Data Protection Regulation (GDPR) |
EU |
An EU regulation, it imposes obligations onto organizations anywhere, as long as they target or collect data related to people in the EU |
|
Data Protection Act |
UK |
The UK’s implementation of GDPR controls how personal information is used by organizations, businesses, or the government |
|
California Consumer Privacy Act (CCPA) |
California, US |
A state statute intended to enhance privacy rights and consumer protection for residents of California, US |
|
General Data Protection Law (LGPD) |
Brazil |
Addresses the processing of personal data, including by digital means, by a natural person or a legal entity of either public or private law |
|
Personal Information Protection and Electronic Documents Act (PIPEDA) |
Canada |
Applies to private sector organizations across Canada that collect, use, or disclose personal information in the course of a commercial activity |
|
Privacy Act |
Australia |
Promotes and protects the privacy of individuals and regulates how Australian government agencies and organizations handle personal information |
Source: Omdia
There are plenty of examples of breaches of data privacy legislation. A significant fine of €390m was issued to Meta (owner of Facebook) for breaking EU data laws on using personal data to deliver targeted advertisements. The ruling rejected Meta’s argument that when people engage with social media platforms, accepting terms and conditions, they are in fact agreeing to receive personalized ads. The ruling was made just this month (January 2023), and Meta plans to appeal the decision.
In the UK, the UK Information Commissioner’s Office (ICO) fined The Tavistock & Portman NHS Foundation Trust. The ICO reported that “Between the period 25 May 2018 to 6 September 2019, the Trust used Outlook to send bulk emails to 1,781 Gender Identity Clinic service users. The Trust failed to comply with Chapter II GDPR and was fined £78,400 in June 2022.” In Omdia’s opinion this is a process failure, where a data privacy officer (a role required by GDPR) has not ensured that due process is being followed for contacting individuals via the details an organization holds.
Another UK ICO fine was for £98,000, issued to Tuckers Solicitors LLP in March 2022. The ICO reported the following:
During the period of 25 May 2018 to 25 August 2020 (‘the relevant period’), Tuckers failed to process personal data in a manner that ensured appropriate security of the personal data, including protection against unauthorized or unlawful processing and against accidental loss, destruction, or damage, using appropriate technical or organizational measures. Tuckers became aware on 24 August 2020 of a ransomware attack on its systems, and on 25 August 2020 determined that the attack had resulted in a personal data breach. The Commissioner considers that Tuckers' failure to implement appropriate technical and organization measures over some or all of the relevant period rendered it vulnerable to the attack.
In Omdia’s opinion this points to more of a failure of cyber-hygiene: not adequately protecting PII.
Customer demands for data privacy
Some consumers are becoming more “savvy” about their data and how it should be kept private. However, apathy and lack of knowledge are also evident among customers when it comes to data privacy: many are not always aware of what they are signing up to or not caring what they are signing up to because they get something free.
In many parts of the world, if a company breaches data privacy regulations they must inform their customers and support them. There are, however, many organizations that take their time to report breaches, and especially if they have not created a playbook for such a situation, they may struggle to follow the right and appropriate rules, let alone handle any press inquiries, deal with ransomware demands, and so on.
There are also more examples of legal firms offering no-win no-fee products to act on behalf of individuals to obtain compensation for data privacy breaches.
It is incumbent upon those responsible for data privacy at an organization to look after their customers’ data in the same way that they would expect other organizations to look after personal data about them. There is no doubt that maintaining data privacy is a challenge, but it must be tackled head on as a component of winning and maintaining customer trust.
Resilience must be the foundation of data privacy efforts
Innovation will continue: Data must be secured alongside
Digital dependence has been brought about by consumer and business demand for digital technology. This situation has evolved rapidly over the past two decades, most especially since the launch of the iPhone in 2007. Digital dependence is not a bad thing—it gives businesses and consumers access to better products and services—but it does require digital resilience. Digital resilience is described by Omdia as “the ability to continuously operate and quickly leverage digital opportunities.” This requires cyber-resilience, described by Omdia as “a core component of digital resilience. It ensures that the organization continuously operates despite security incidents and breaches.”
Note “despite security incidents and breaches.” There is increasing acceptance that it is not a question of if a security incident or breach will happen but when. It is nigh-on impossible to close every virtual door and shut every virtual window without disconnecting from the outside world completely, which for almost every organization is not feasible if it wants to be able to operate. Instead, organizations focus on their own risk appetite, in line with regulations.
While the primary purpose of the early internet was data transmission, the need to effectively secure the data itself was initially overlooked. It was not until after the carnage from years of costly data theft, victimizing government institutions and private organizations alike, that the need for data security solutions was fully recognized. It was from this requirement that the confidentiality, integrity, availability (CIA) trinity of cybersecurity was spawned to mitigate the risks of unsanctioned disclosure of data (confidentiality), unauthorized alteration or modification of data (integrity), or disruption of legitimate access to data (availability). Moreover, because protocols to facilitate secure data transmission were not baked into the internet by default, many of the data security solutions that have been implemented in the 21st century have been deployed in an inefficient and piecemeal manner.
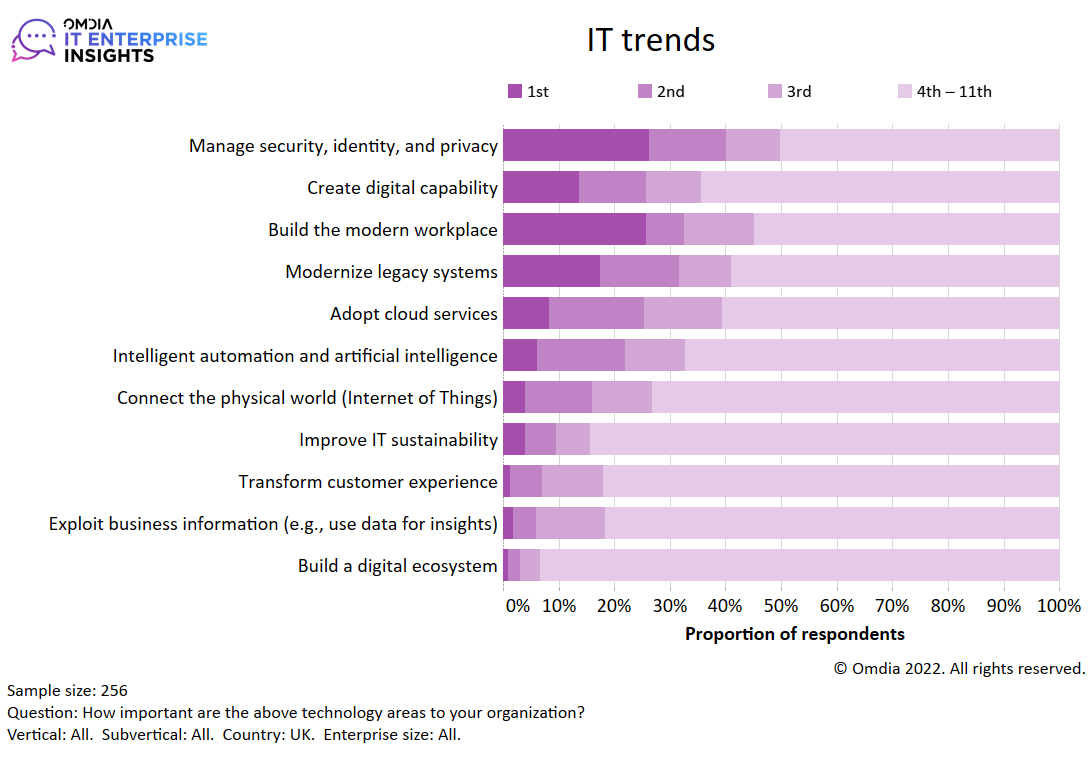
Omdia’s annual IT Enterprise Insights survey for 2022/23, published in November 2022, shows that the management of security, identity, and privacy tops the list of IT trends, a top-three priority for 53% of organizations, but is closely followed by the need to create digital capabilities and build the modern workplace, taking advantage of innovation. Indeed, the creation of digital capability is the leading top priority, identified by 23% of organizations (see Figure 4).
Figure 4: Omdia IT Enterprise Insights 2022/23, top IT trends
 Source: Omdia Enterprise Insights 2022/23
Source: Omdia Enterprise Insights 2022/23
Despite economic uncertainty, innovation will continue: there is no lack of desire to continue innovating. Figure 4 shows that organizations recognize the importance and value of innovation using digital technologies while simultaneously recognizing the need to managed security, identity, and privacy.
The same survey also shows how survey respondents rate their organization’s progress in managing security, identity, and privacy. Globally, 61% of organizations describe themselves as well advanced or advanced. This of course leaves 39% of organizations with a substantially inadequate approach to the management of security, identity, and privacy.
Know what data you have, how to govern it, and how to protect it
In no small part, data security focuses on maintaining data privacy. Data security is essential to the fundamental ideas of information ownership, which are dependent on a comprehensive strategy and comprise three primary elements:
- Data discovery is needed to successfully locate information assets that may require protection.
- Data governance is necessary to ensure that data is managed properly while internal policies are adhered to and external compliance requirements are met.
- Data protection is essential to prevent information from being accessed or potentially compromised by unauthorized parties.
Effective information security demands granular control over the comprehensive handling of data throughout its entire lifecycle: create, process, store, transmit, and destroy (see Figure 5).
Figure 5: The information lifecycle
 Source: Omdia
Source: Omdia
As organizations generate ever-increasing volumes of data, proper data handling requires a comprehensive understanding of how data lifecycle activities affect the data footprint and an understanding of their respective responsibilities throughout each step.
Despite the concerted efforts associated with discovering and classifying data, imposing controls over its lifecycle, and ultimately, dictating how it is used, these endeavors can be rendered moot if one of the most fundamental components of governance, effective data backup and storage, is ignored. Adversaries have proved to be more than willing to capitalize on the poor data backup practices that many organizations continue to engage in.
Ultimately, organizations must focus on data security to have a hope of maintaining the confidentiality of the information they are responsible for, thus adhering to data privacy regulations and expectations.
Proper preparation and planning prevent poor performance
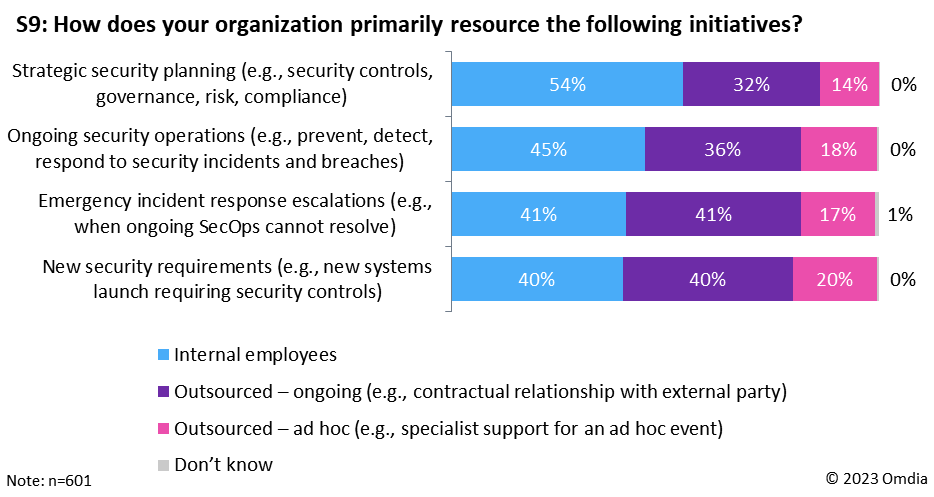
Alongside the direct focus on data security, the acknowledgment that security incidents and breaches will happen means that CISOs must lean into incident response and preparedness. Omdia’s Cybersecurity Decision Maker survey shows that, given the challenges in resourcing, 41% of organizations use specialist support for ad hoc events (see Figure 6).
Figure 6: Omdia Cybersecurity Decision Maker survey, resourcing for security requirements
 Source: Omdia
Source: Omdia
As can be seen from Figure 6, there is widespread use of contracted and ad hoc outsourcing partners to bolster organizations’ security capabilities. Omdia fully expects this to continue and even grow, because we know (from Omdia’s IT Enterprise Insights survey) that managed security services is the leading area of security investment, with 65% of organizations planning strategic or minor investment.
Organizations frequently use suppliers to help them with all aspects of cybersecurity, including the management of data privacy.
Appendix
Further reading
Data Privacy Day 2022: Ransomware’s Success is Data Privacy’s Failure (January 2022)
Author
Maxine Holt, Senior Director, Cybersecurity

